Manage AMT Device
-
Go back to the Sample Web UI on your development system.
-
Click the Devices tab from the menu on the left.
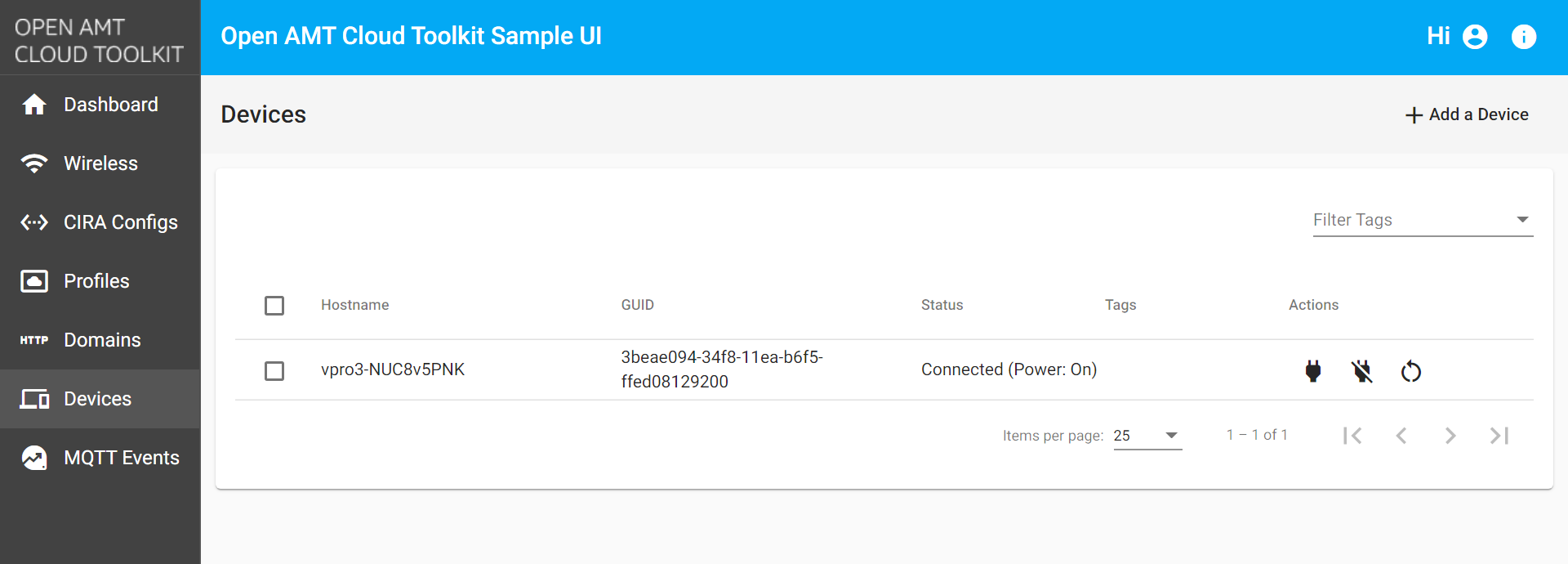
Figure 1: Devices tab Troubleshooting
If the activated device is not listed or if it is listed as unconnected, try restarting the AMT device. After successfully restarting the device, refresh the Sample Web UI to see if the Status changes to connected.
-
Click on your connected device.
-
Select an action to perform from the options in the top-right.
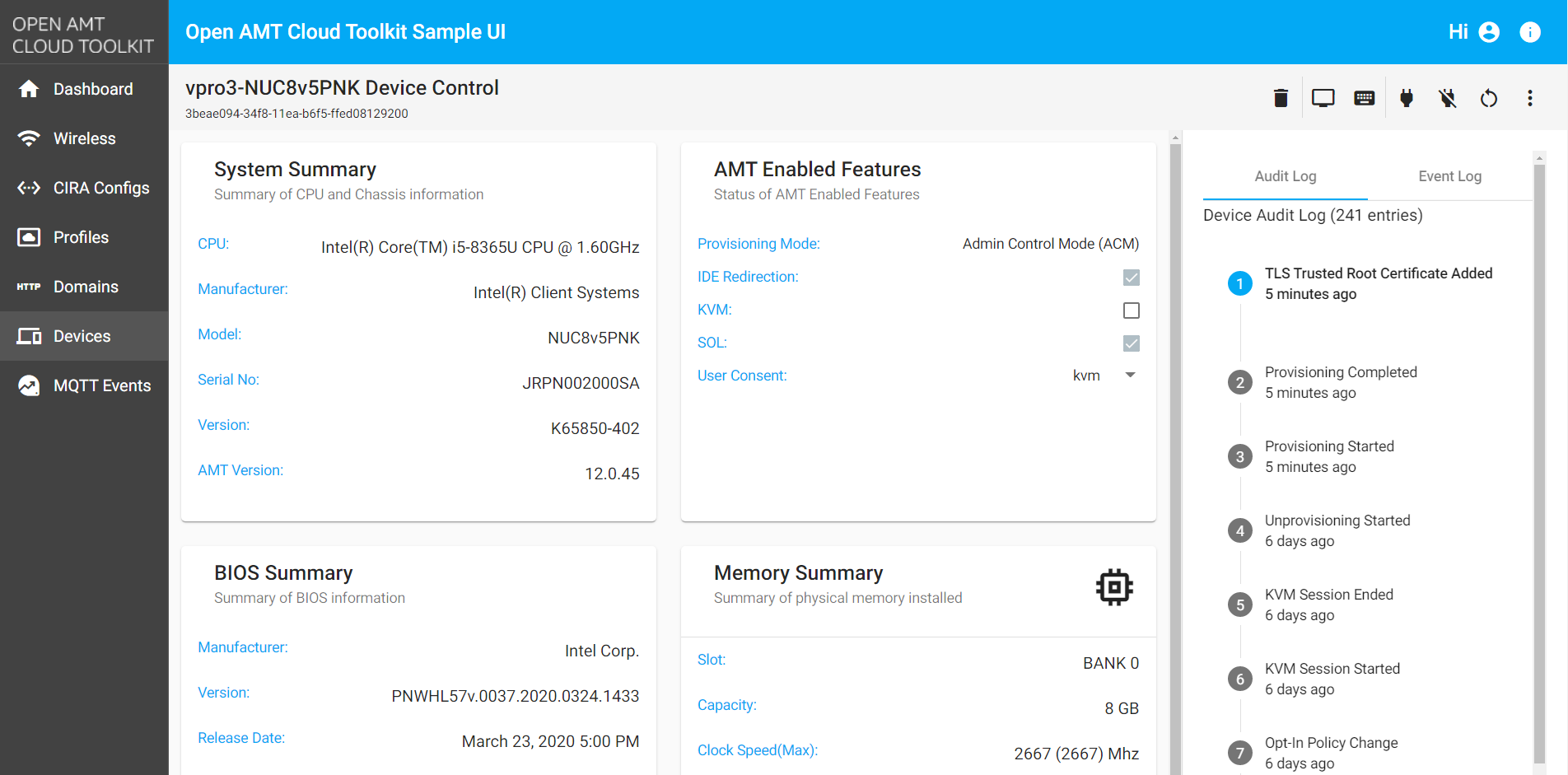
Figure 2: Action options Note
If activated in Client Control Mode(CCM), the keyboard, video, mouse (KVM) and serial over LAN (SOL) features require entering a user consent code, which will be displayed on the device. To use KVM/SOL without user consent, follow the ACM Activation Path for how to configure a device into Admin Control Mode.
Warning
Turn off active redirection sessions, such as KVM or SOL, before power state transitions. Power Cycle Reset and Unconditional Power Down (Power Off) will be rejected as invalid if there is an active redirection session.
-
When performing a KVM action for a device activated in CCM or ACM with user consent enabled, input the user consent code displayed on the client device.
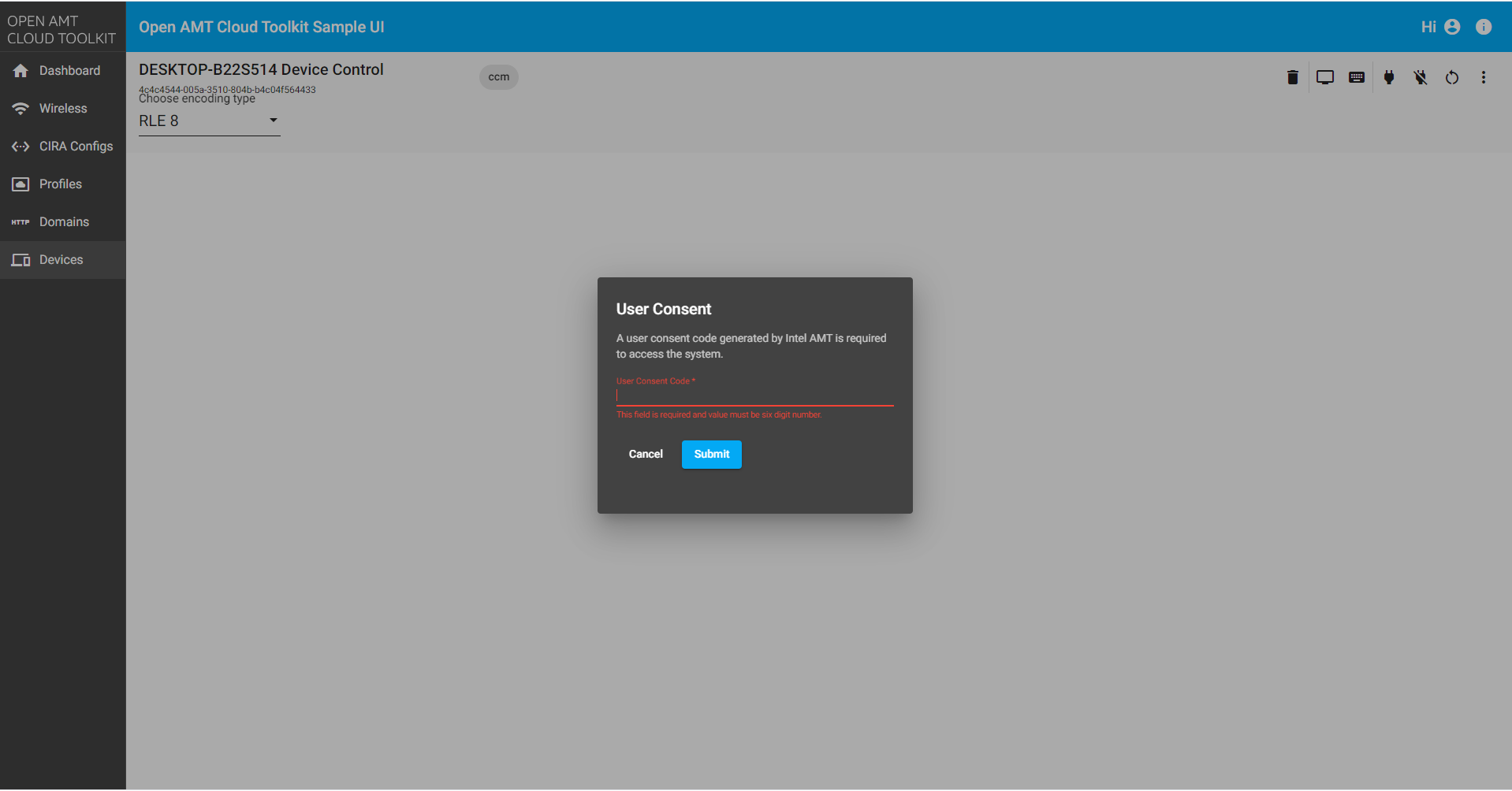
Figure 3: User Consent
Next steps¶
After successfully deploying the Open AMT Cloud Toolkit microservices and client, explore other tools and topics in the Open AMT Cloud Toolkit architecture:
REST API Calls¶
Learn how to send commands to AMT devices with the curl-based REST API tutorial. Generate a JWT token for Authorization and construct an API call to get a list of devices.
Get Started with REST API Calls
UI Toolkit¶
Explore the Open AMT Cloud Toolkit reference implementation console by adding manageability features with prebuilt React components, such as Keyboard, Video, and Mouse (KVM).
Get Started with the UI Toolkit
Security¶
Learn how to use the Open AMT Cloud Toolkit architecture to secure assets. Topics include credentials, allowlisting, best known security methods, and more.